Matlab Code for LSB Steganography
₹3,000.00
Huge Price Drop : 50% Discount
Source Code + Demo Video
100 in stock
Description
LSB ALGORITHM
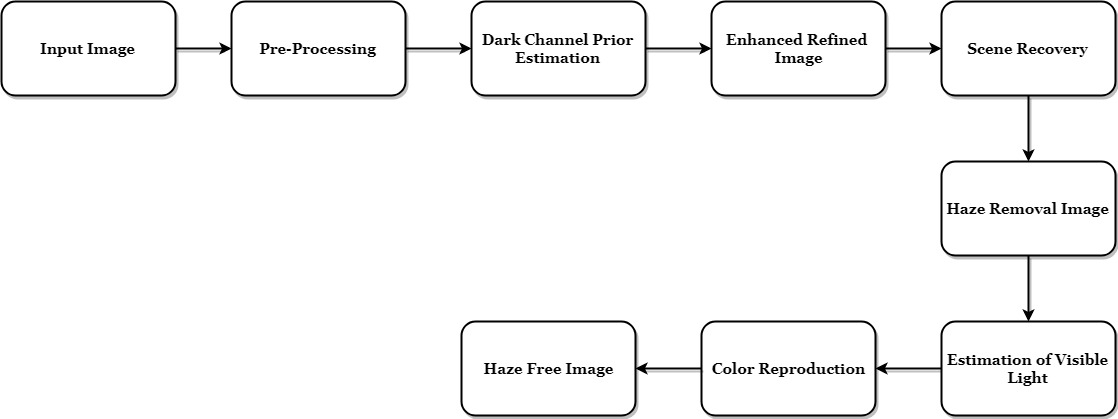
Steganography is a branch of information hiding. It allows the people to communicate secretly. As increasingly more material becomes available electronically, the influence of steganography on our lives will continue to grow. Many confidential information were leaked to a rival firm using steganographic tools that hid the information in music and picture files. The application of steganography is an important motivation for feature selection. A new steganographic algorithm for 8bit (grayscale) or 24bit (colour image) is presented in this article, based on Logical operation. Algorithm embedded Ascii code of text in to LSB of cover image.
DEMO VIDEO
Cover-Image: An image in which the secret information is going to be hidden. The term “cover” is used to describe the original, innocent message, data, audio, still, video etc. The cover image is sometimes called as the “host”.
Stego-Image: The medium in which the information is hidden. The “stego” data is the data containing both the cover image and the “embedded” information. Logically, the processing of hiding the secret information in the cover image is known as embedding.
Payload: The information which is to be concealed. The information to be hidden in the cover data is known as the “embedded” data.
Secret key: This is the key used as a password to encrypt and decrypt the cover and stego respectively in order to extract the hidden message. Secret key is optional.
ABSTRACT
A lossless data hiding technique using LSB in images is presented in this paper. LSB data hiding technique does not affect the visible properties of the image. Steganography is art and science of hiding the fact that communication is taking place. Secrets can be hidden in all types of medium: text, audio, video and images. Steganography is an important area of research in recent years involving a number of applications. It is the science of embedding information into the cover image viz., text, video, and image (payload) without causing statistically significant modification to the cover image. The modern secure image steganography presents a challenging task of transferring the embedded information to the destination without being detected. This paper deals with hiding text in an image file using Least Significant Bit (LSB) technique. The LSB algorithm is implemented in spatial domain in which the payload bits are embedded into the least significant bits of cover image to derive the stego-image.
INTRODUCTION
The spread of wireless Internet-based services such as introduction of the fourth-generation mobile communication systems, user can transfer data up to 1Gbps .Due to the availability of low cost editing tools, digital data can be easily copied, modified and retransmitted in the network by any user. To effectively support the growth of multimedia communications, it is essential to develop tools that protect and authenticate digital information. In this contribution, we present a novel embedding scheme based on the LSB technique. If the value of the pixel of an image is changed by a value of ‘1’ it does not affect the appearance of the image. This idea helps us to for hiding data in an image.
EXISTING SYSTEM
We used to go just with the bit replacement process of encrypting and decrypting data
PROPOSED SYSTEM
The image steganography is the process in which we hide the data within an image so that there will not be any perceived visible change in the original image. The conventional image steganography algorithm is LSB embedding algorithm
BLOCK DIAGRAM
ADVANTAGES
Steganography has unique advantages for net-espionage agents. Even if a file is known or suspected to contain Steganographic software, it is almost impossible to extract the information until the correct password is obtained. Steganography is beneficial for securely storing sensitive data, such as hiding system passwords or keys within other files. In places where standard cryptography and encryption is outlawed, Steganography can be used for covert data transmission.
APPLICATIONS
Steganography can be used in supplementary to cryptography, watermarking and fingerprinting. Steganography can be used to conceal and transfer an encrypted document containing some acquired information in military applications.
CONCLUSION
Still efforts have to be made to increase the embedding capacity and maintain secrecy. In this method we can hide text file equal to the size of the image. Efforts can be made to hide text files having more size than image size. The secret keys have to be known to both sender and receiver. Keys are not sent in cover-images but are distributed separately. A technique can be evolved so that these keys can be generated and distributed covertly. The Transform Domain method can be utilized if more security is required.
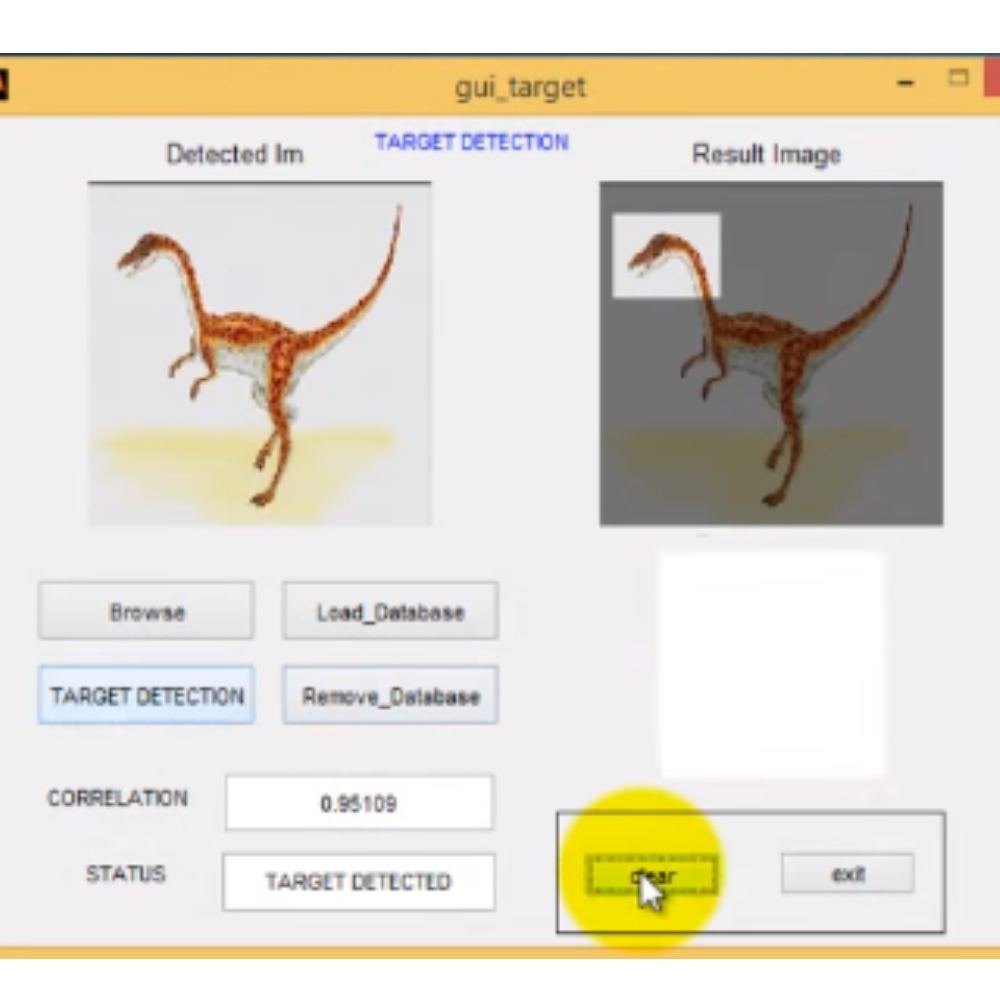
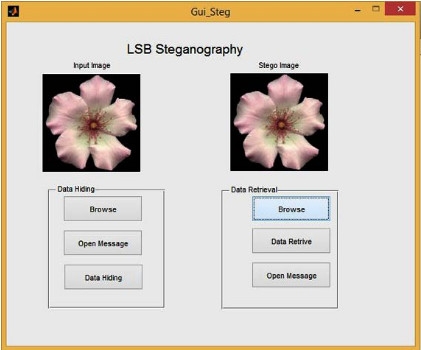
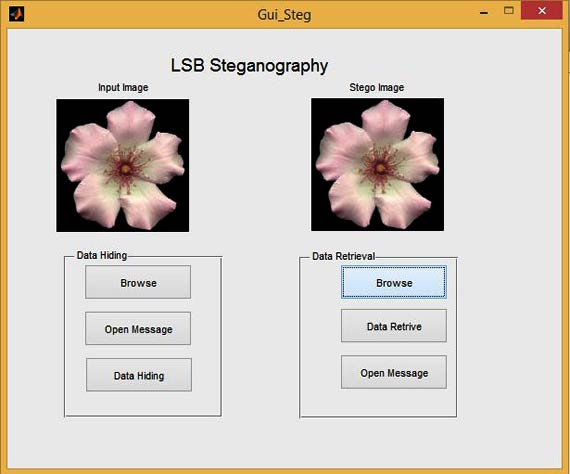
GUI FOR LSB STEGANOGRAPHY
REFERNCES
[1] Vasco Pereira and Tiago Sousa, “Evolution of Mobile Communications: from 1G to 4G”, in Proc. Of The 2nd International Working Conference on Performance Modeling and Evaluation of Heterogeneous Networks, HET-NETs’04, West Yorkshire, U.K., July 2004
[2] http://studentweb.niu.edu/9/~Z172699/Description.html
[3] M. Pavani1, S. Naganjaneyulu, C. Nagaraju, ”A Survey on LSB Based Steganography Methods” International Journal Of Engineering And Computer Science ISSN:2319-7242 Volume 2 Issue 8 August, 2013 Page No. 2464-2467
[4] Stuti Goel, Arun Rana, Manpreet Kaur,”A Review of Comparison Techniques of Image Steganography”, IOSR Journal of Electrical and Electronics Engineering (IOSR-JEEE) e-ISSN: 2278-1676,p-ISSN: 2320-3331, Volume 6, Issue 1 (May. – Jun. 2013), PP 41-48
[5] http://dimabatenkov.info/ssis_project/methods.htm
[6] http://dhsprojects.blogspot.in/2012/08/ieee-2012-separable-reversible-data.html
[7] A. I. Kahdum, ”IBN AL-HAITHAM Journal for pure & applied Science”, Vol.21(1) 2008
[8] http://studentweb.niu.edu/9/~Z172699/Description.html
[9] Diego De Luca Picione , Federica Battisti , Marco Carli ,Jaakko Astola , and Karen Egiazarian,”A FIBONACCI LSB DATA HIDING TECNIQUE”,14th European Signal Processing Conference (EUSIPCO 2006), Florence, Italy, September 4-8, 2006, copyright by EURASIP
[10] http://imagelpcmatlab.blogspot.in/2013/12/matlab-implementation-of-steganography.html
[11] http://www.asciitable.com/
[12] http://www.viprefect.com/application-areas
[13] http://studentweb.niu.edu/9/~Z172699/Conclusion.html
For more Image Processing projects ,Click here






Reviews
There are no reviews yet.