Biometric Security System Using Palmprint And Cryptanalysis
₹3,000.00
Huge Price Drop : 50% Discount
Source Code + Demo Video
Platform : Matlab
Delivery : One Working Day
Support : Online Demo ( 2 Hours)
100 in stock
Description
ABSTRACT
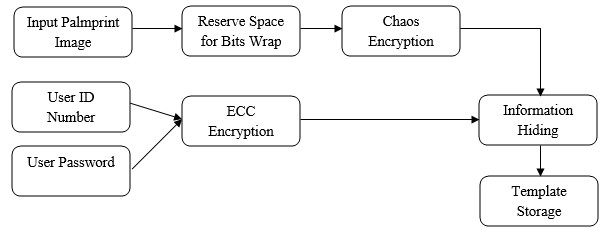
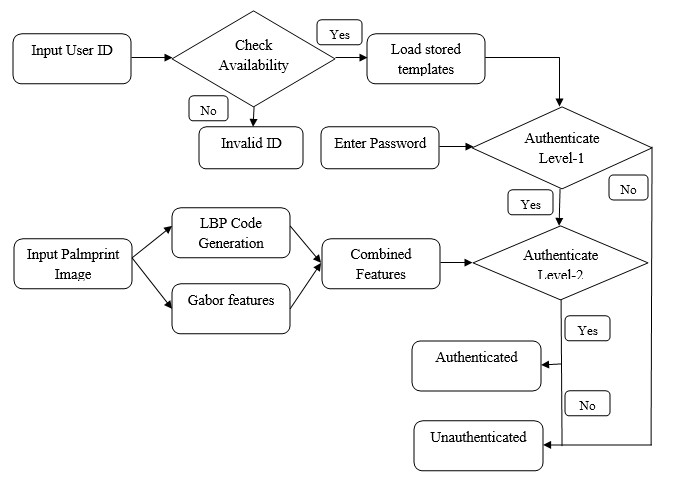
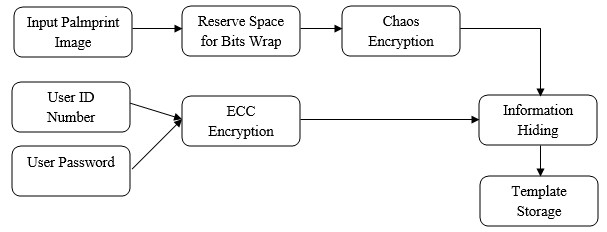
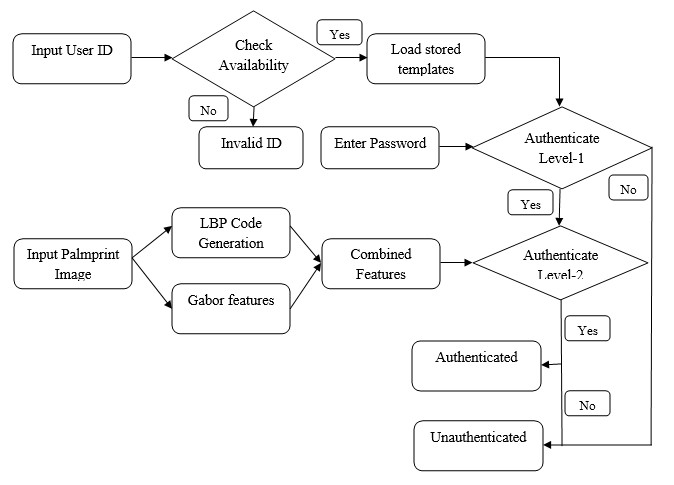
The project presents robust person authentication scheme based on palmprint biometrics and hybrid cryptographic techniques. The security system involves the techniques of steganography, cryptography and pattern recognition. A Biometric system is essentially a pattern recognition system that makes use of biometric traits to recognize individuals. One of the most useful personal biometric is palmprint which consists of more sufficient features points for individual unique identification. Palm is the inner surface of a hand between the wrist and the fingers. Palmprint is referred to principal lines, wrinkles and ridges on the palm. The system has two phases such as user registration phase and authentication phase. User registration phase is for enrolling person privacy data with their biometric. Next these data’s are encrypted using public key type elliptical curve cryptography and this confidential information concealed into person palmprint 2D image using effective steganographic algorithm called bits substitution method. In order to minimize the error between original and stego image, reserving coefficients will be done via lifting wavelet decomposition before image encryption. Here, the palmprint image will be encrypted using symmetric key chaos encryption. In authentication phase, recognition will be performed through two levels such as password matching and palmprint matching. The palmprint texture will be characterized using two effective local descriptors Local binary pattern codes and Gabor filter bank. These combined features are utilized to match input and already stored templates. If the two of these authentications is successful then the person gets authenticated otherwise not authenticated. The simulated system shows that a used methodology provides better information security and texture analysis rather than prior approaches.
EXISTING METHODS
- Fingerprint based person authentication
- RSA public key cryptography
- Discrete wavelet transform
- Weber’s Local descriptors
DRAWBACKS
- Less efficiency and not flexible in authentication scheme
- High computational load when key size increases
- Inefficient texture features due to shift variance
- Less accuracy for various lighting condition of images due to the delivery of insufficient descriptors.
PROPOSED METHODS
An efficient biometric security system using palmprint recognition and person information protection based on,
- Local binary pattern and Gabor filter based texture analysis
- Chaos and Elliptic curve cryptosystem
METHODOLOGIES
- Chaos crypto system
- Elliptic curve Cryptography
- Bits Substitution approach
- LBP Code and Gabor filter
BLOCK DIAGRAM
REGISTRATION PHASE
AUTHENTICATION PHASE
ADVANTAGES
- More information security via hybrid crypto systems
- Better texture characterization of palmprint
- High efficiency and low complexity
APPLICATIONS
- Defense weapon storage Area
- Bank ATM security
- Authentication and privacy protection
SOFTWARE REQUIREMENT
- MATLAB 7.5 and above versions
RESULTS
REFERENCES
[1] A. K. Jain, A. Ross, and S. Prabhakar, “An introduction to biometric recognition,” IEEE Trans. Circuits Syst. Video Technol., vol. 14, no. 1, pp. 4–20, Jan. 2004.
[2] D. Maltoni, D. Maio, A. K. Jain, and S. Prabhakar, Handbook of Fingerprint Recognition. New York, NY, USA: Springer-Verlag, 2009.
[3] S. Prabhakar, S. Pankanti, and A. K. Jain, “Biometric recognition: Security and privacy concerns,” IEEE Security Privacy Mag., vol. 1, no. 2, pp. 33–42, Mar./Apr. 2003.
[4] X. Li, J. Niu, and M. K. Khan, “Robust Biometrics Based Three-Factor Remote User Authentication Scheme with Key Agreement,” in Proc. IEEE Int. Symp. Biometr. Security Technol., 2013, pp. 105–110.
[5] N. D. Sarier, “Generic constructions of biometric identity based encryption systems,” in Proc. Security Privacy Mobile Devices Wireless Commun., 2010, pp. 90–105.
[6] N. D. Sarier, “A new biometric identity based encryption scheme secure against DoS attacks,” Security Commun. Netw., vol. 4, no. 1, pp. 23–32, Jan. 2011.
[7] A. Burnett, F. Byrne, T. Dowling and A. Duffy, “A biometric identity based signature scheme”, Int. J. Netw Security, vol. 5, no. 3, pp. 317–326, 2007.
[8] Y. Yang, Y. Hu, and L. Zhang, “An efficient biometric identity based signature scheme,” KSII Trans. Internet Inf. Syst., vol. 7, no. 8, pp. 2010– 2026, Aug. 2013.
Additional information
| Weight | 0.000000 kg |
|---|



Reviews
There are no reviews yet.