A Practical wireless Attack On The Connected Car And Security Protocol For In-Vehicle CAN
Call for Price
A Practical wireless Attack On The Connected Car And Security Protocol For In-Vehicle CAN
Description
Abstract :
Vehicle-IT convergence technology is a rapidly rising paradigm of modern vehicles, in which an electronic control unit (ECU) is used to control the vehicle electrical systems, and the controller area network (CAN), an in-vehicle network, is commonly used to construct an efficient network of ECUs. Unfortunately, security issues have not been treated properly in CAN, although CAN control messages could be life-critical. With the appearance of the connected car environment, in-vehicle networks (e.g., CAN) are now connected to external networks (e.g., 3G/4G mobile networks), enabling an adversary to perform a long-range wireless attack using CAN vulnerabilities. In this paper we show that a long-range wireless attack is physically possible using a real vehicle and malicious smart phone application in a connected car environment. We also propose a security protocol for CAN as a countermeasure designed in accordance with current CAN specifications. We evaluate the feasibility of the proposed security protocol using CAN and a lpc2148 microcontroller. Our results show that the proposed security protocol is more efficient than existing security protocols with respect to authentication delay and communication load..
Existing System :
- In this system sakura board is used. Sakura board uses an RX63N microcontroller.
Disadvantages :
- Manual operation
- Monitoring depends on driver
- Less Alert system
- Unsafe for others
Proposed System :
- Along with ARM controller to monitor and diagnose the problems in VEHICAL.
Advantages :
- Automatic operation
- safety concerns for others
- Continuously monitor with sensors& high alert system
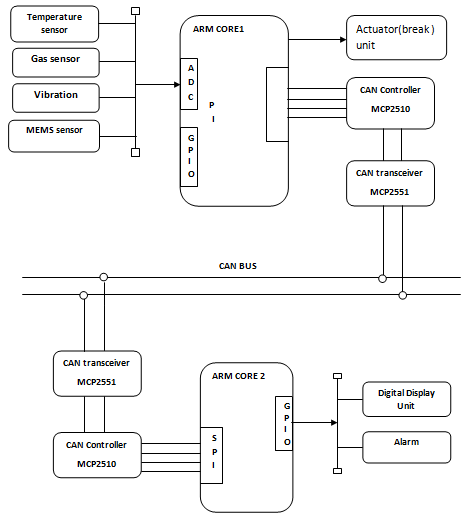
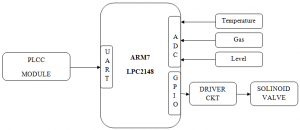
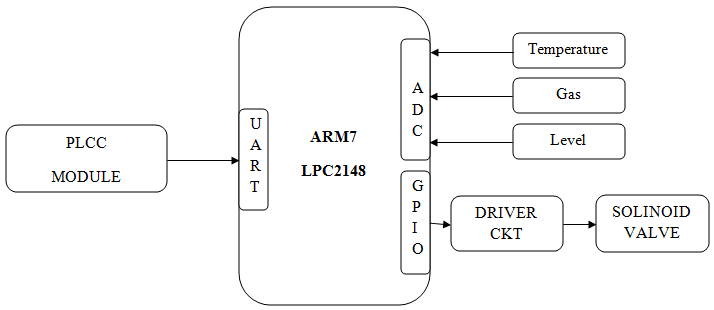
Block Diagram :
The system consists of microcontroller, CAN controller and parameters of VEHICAL. Microcontroller is the key element in processing module which keeps on monitors the VEHICAL parameters. In the VEHICAL temperature sensor, MEMS sensor and are connected to monitor the physical parameter of the VEHICLE. CAN controller is used to communicate between the wind turbine and the database. For every particular amount of time, microcontroller pre-processes sensed data and it will update the parameter values to the central database. RS232 is used for serial communication between the PC and the CAN Bus. CAN interface module is used to communicate the monitored parameters between the VEHICLE and the control centre. The CAN interface module consists of three components CAN Transceiver (MCP 255 1), CAN Controller (MCP 25 10), DSPIC. CAN transceiver is required to shift the voltage levels of the microcontroller to those appropriate for the CAN bus.
Hardware :
- ARM LPC2148
- MEMS Accelerometer
- Vibration
- Temperature sensor
- CAN controller MCP2510
Software :
- Compiler(KEIL IDE)
- Orcad design
- Programmers(Flash Magic)
- Languages: Embedded C
Applications :
- Electrical applications
- Industrial applications
- RTOS applications
Additional information
| Weight | 1.000000 kg |
|---|
This site uses Akismet to reduce spam. Learn how your comment data is processed.
Related products
-
- Read more
- Embedded Projects, Projects
PLCC Based Boiler Monitoring
- Call for Price
- Rated 0 out of 5
-
- Out of StockRead more
- FPGA Projects, Projects
Bluetooth based RC car control using Spartan3an FPGA Project Kit
- Call for Price
- Rated 0 out of 5
-
-
- Out of StockRead more
- FPGA Projects, Projects
CPU Fan speed control based on IC temperature using Spartan6 FPGA Project Kit
- Call for Price
- Rated 0 out of 5
-


Reviews
There are no reviews yet.